AJAX - Security: CORS, CSRF Tokens & XSS Mitigation Strategies
1. Why Security Is Critical in AJAX Applications
AJAX allows a web page to:
-
Communicate with servers silently
-
Send and receive sensitive data (login, payments, profiles)
If security is weak:
-
Data can be stolen
-
User accounts can be hijacked
-
Malicious actions can be performed without user knowledge
That is why CORS, CSRF protection, and XSS prevention are essential.
PART A: CORS (Cross-Origin Resource Sharing)
2. What Is CORS? (Quick Recap)
CORS controls:
Which external websites are allowed to access your server’s data using AJAX.
Browsers block cross-origin requests by default for safety.
3. Why CORS Is a Security Feature
Without CORS:
-
Any website could read private APIs
-
User data could be leaked
CORS ensures:
-
Only trusted origins can access resources
-
Server explicitly grants permission
4. Important CORS Security Rules
✔ Do not use:
Access-Control-Allow-Origin: *
for private APIs
✔ Allow only trusted domains
✔ Be careful with:
Access-Control-Allow-Credentials: true
5. Exam Line (CORS)
CORS is a browser-enforced security mechanism that restricts cross-origin AJAX requests unless explicitly allowed by the server.
PART B: CSRF (Cross-Site Request Forgery)
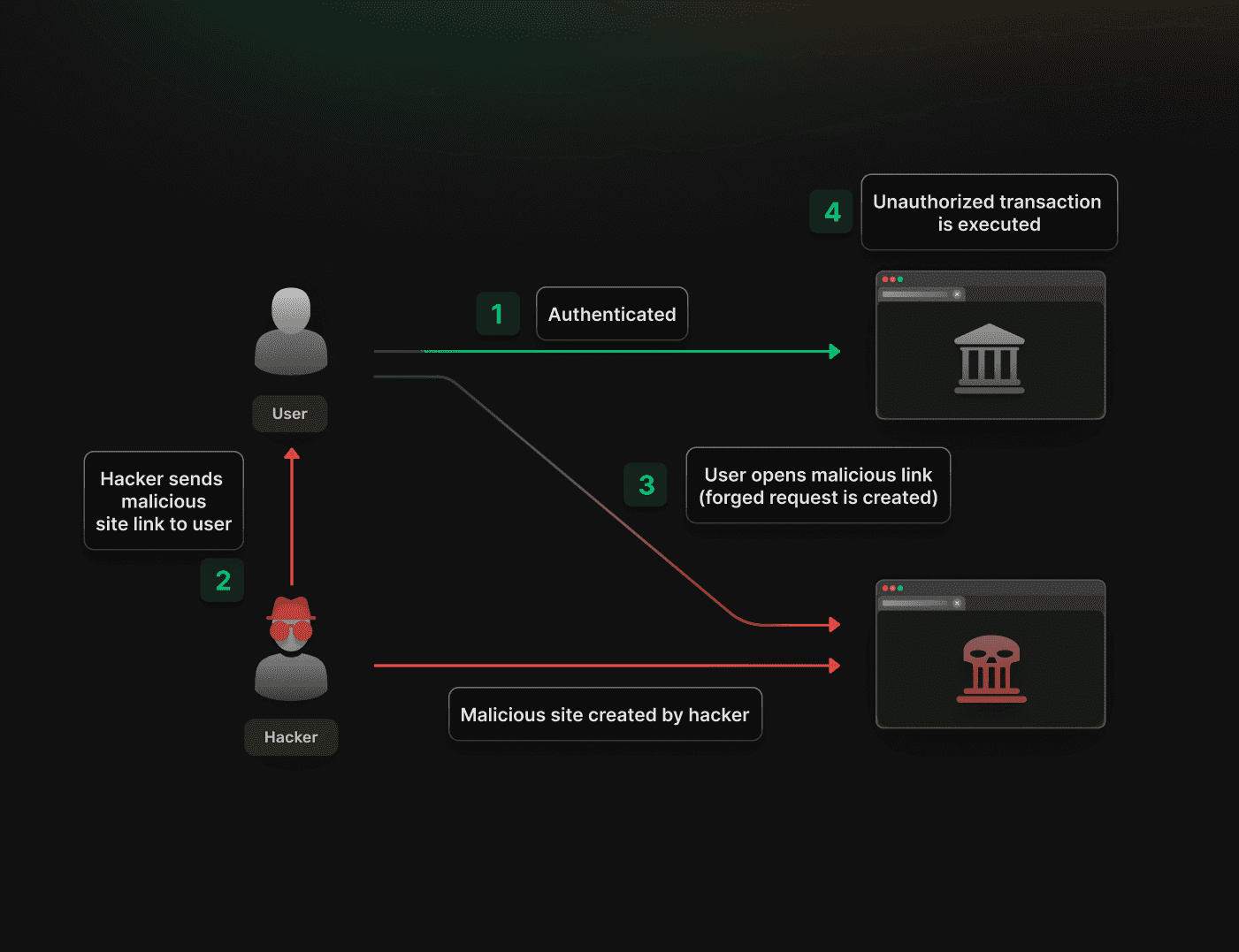
6. What Is CSRF? (Very Important)
CSRF is an attack where:
A malicious website tricks a logged-in user’s browser into sending an unwanted request to a trusted website.
The browser automatically sends:
-
Cookies
-
Session IDs
This is the danger.
7. CSRF Attack Example (Easy)
-
User logs into bank.com
-
Cookie is stored in browser
-
User visits evil.com
-
evil.com sends a hidden request to bank.com
-
Browser attaches cookie automatically
-
Money transfer happens ❌
User never clicked anything on bank.com.
8. How CSRF Tokens Prevent This
A CSRF Token is:
-
A random, secret value
-
Generated by the server
-
Sent with every sensitive request
Only the real website knows this token.
9. CSRF Protection Flow
-
Server sends token to client
-
Client includes token in AJAX request
-
Server verifies token
-
Request accepted only if token is valid
If attacker tries:
❌ Token missing
❌ Token incorrect
→ Request rejected
10. Exam Line (CSRF Token)
A CSRF token is a unique, secret value used to verify that a request originates from a trusted client.
PART C: XSS (Cross-Site Scripting)
11. What Is XSS?
XSS happens when:
Malicious JavaScript is injected into a trusted website and executed in a user’s browser.
This allows attackers to:
-
Steal cookies
-
Hijack sessions
-
Modify page content
12. Types of XSS (Must Remember)
| Type | Explanation |
|---|---|
| Stored XSS | Malicious script saved in database |
| Reflected XSS | Script comes from URL/request |
| DOM XSS | Client-side JavaScript vulnerability |
13. Simple XSS Example
If user input is displayed directly:
<script>alert("Hacked")</script>
Browser executes it ❌
This is XSS.
14. How to Prevent XSS (Mitigation Strategies)
✔ Escape user input
✔ Never trust client data
✔ Use safe DOM methods (textContent, not innerHTML)
✔ Validate input on server
✔ Use Content Security Policy (CSP)
15. Why XSS Is Dangerous with AJAX
-
AJAX updates content dynamically
-
If unsafe data is injected → instant execution
-
Single mistake can compromise all users
16. CORS vs CSRF vs XSS (Exam Comparison Table)
| Aspect | CORS | CSRF | XSS |
|---|---|---|---|
| Type | Browser security rule | Request forgery attack | Code injection attack |
| Affects | Cross-origin access | Authenticated users | End users |
| Protection | Server headers | CSRF tokens | Input sanitization |
| Related to AJAX | Yes | Yes | Yes |
17. One-Line Exam-Friendly Definitions
-
CORS:
A browser security mechanism that controls cross-origin AJAX access.
-
CSRF:
An attack that forces a user’s browser to perform unwanted actions on a trusted site.
-
XSS:
A vulnerability where malicious scripts are injected and executed in a trusted web page.
18. Key Exam Memory Tip
CORS protects APIs, CSRF protects actions, and XSS protects users.